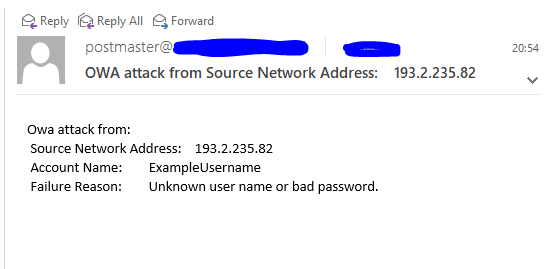
Just for fun I tried to establish a mechanism that will allow me to get information for failed logon attempt on Outlook Web Access (OWA).
If you open event viewer on your CAS server (where OWA is located) you can find out that failed requests are logged with Event ID 4625.
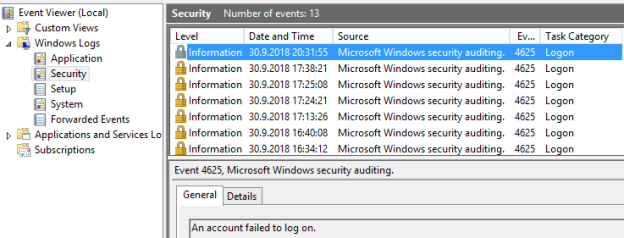
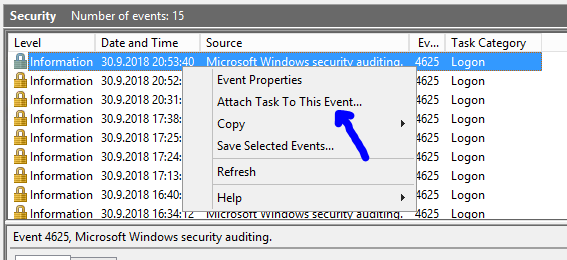
In general information you can find interesting things like – username which was used and IPv4 or IPv6 address from where the attempt was made.
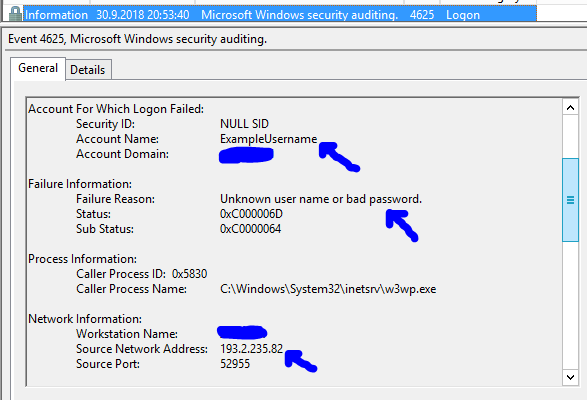
All you need to do is to Attach task to this event
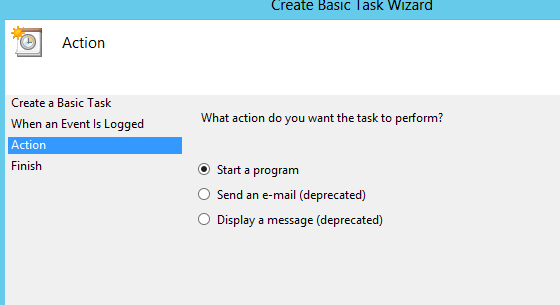
As all other actions are deprecated you should use the option to Start a program – here we will run a Powershell script to do the job.
We need to create a PS1 (powershell script) with content:
$EventMessage = get-winevent -FilterHashtable @{Logname=’Security’;ID=4625} -MaxEvents 1 | fl TimeCreated, Message
$eventmessagetstring = $EventMessage | Out-String
$EventMessageAccountNameText3array = $EventMessagetstring | Select-String -Pattern “Account Name:\s+\S+” -AllMatches | Select -ExpandProperty matches | Select -ExpandProperty value
$EventMessageAccountNameText3 = $EventMessageAccountNameText3array[-1]
$EventMessageAccountNameText = $EventMessagetstring | Select-String -Pattern “Failure Reason:\s+\S+\s+\S+\s+\S+\s+\S+\s+\S+\s+\S+” -AllMatches | Select -ExpandProperty matches | Select -ExpandProperty value
$EventMessageAccountNameText2 = $EventMessagetstring | Select-String -Pattern “Source Network Address:\s+\S+” -AllMatches | Select -ExpandProperty matches | Select -ExpandProperty value
$EmailTo = “admin@domain.com”
$EmailFrom = “alert@domain.com”
$Subject = “OWA attack from $EventMessageAccountNameText2”
$Body = “Owa attack from: `n $EventMessageAccountNameText2 `n $EventMessageAccountNameText3 `n $EventMessageAccountNameText”
$SMTPServer = “IPOfYourSMTPServer”
$SMTPMessage = New-Object System.Net.Mail.MailMessage($EmailFrom,$EmailTo,$Subject,$Body)
$SMTPClient = New-Object Net.Mail.SmtpClient($SmtpServer, 25)
$SMTPClient.Send($SMTPMessage)
So in task properties we should choose:
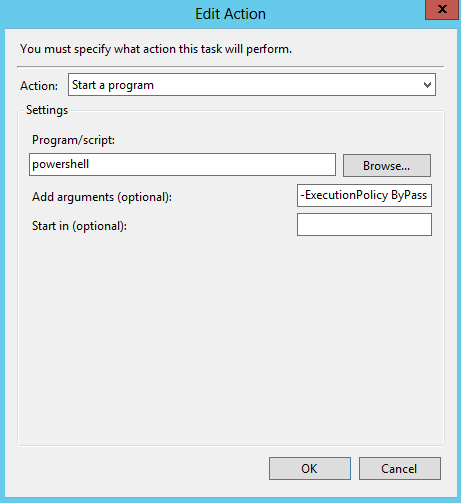
In Add arguments (optional) field we should add:
-ExecutionPolicy ByPass -File X:\PathToScript\OwaAttack.ps1
So if everything is correct – next time someone fail to enter correct password or an attack on OWA is performed you will get an e-mail like this: